

68 Circular Road, #02-01 049422, Singapore
Revenue Tower, Scbd, Jakarta 12190, Indonesia
4th Floor, Pinnacle Business Park, Andheri East, Mumbai, 400093
Cinnabar Hills, Embassy Golf Links Business Park, Bengaluru, Karnataka 560071
Connect With Us
AI-Driven Fraud Prevention in DTC & Marketplaces: Behavioral Biometrics, Deepfake Blocking & Instant Identity Resolution (USA, 2025–2030)
From 2025 to 2030, US eCommerce fraud shifts from card‑centric detection to identity‑first prevention that blends behavioral biometrics, device intelligence, liveness checks, and instant identity graph resolution. Attackers industrialize deepfakes, emulators, and synthetic identities; defenders counter by scoring behavior (keystroke cadence, pointer micro‑motions), verifying government‑ID liveness without friction, and triangulating consented signals from carriers, banks, and trusted identity providers. The objective function moves beyond pure chargeback avoidance toward maximizing instant approvals while keeping false positives and manual reviews low.

What's Covered?
Report Summary
Key Takeaways
1. Identity‑first stacks maximize instant approvals while lowering chargebacks—conversion and risk goals align.
2. Behavioral biometrics plus device intelligence defeat bots/emulators and reduce step‑up friction.
3. Deepfake defenses require liveness (selfie/voice) and ongoing model‑risk tests, not just vendor claims.
4. Graph resolution with consented telco/payment tokens outperforms cookie/device‑ID heuristics.
5. Manual review should be exception‑only with clear escalation paths and feedback loops into models.
6. Bias/fairness tests and adverse‑action notices are essential for compliance and trust.
7. Red‑team simulations (synthetic IDs, emulator farms) harden controls before peak seasons.
8. Telemetry (FPR, chargeback rate, latency, step‑up %) must be finance‑grade and auditable.
Key Metrics

Market Size & Share
Fraud risk and decisioning are two sides of the same market: the share of orders approved instantly becomes a primary competitive metric. In this illustrative outlook, US attack rates decline from ~3.8% of transactions in 2025 to ~2.4% by 2030, while instant‑approval share rises from ~42% to ~76%. Share of prevention spend shifts toward identity‑resolution graphs, behavioral biometrics, and liveness tooling integrated directly into checkout SDKs and payout flows. Marketplaces expand their share of tooling spend as seller onboarding, payout, and KYC become persistent attack targets.
Distribution is bar‑belled: large enterprises standardize stacks and build in‑house decisioning, while SMBs adopt managed‑service models bundled with payments or commerce platforms. Vendors that can prove low latency, high approval precision, and verifiable deepfake blocking capture disproportionate share. By 2030, instant‑approval leadership and low false positives translate directly into higher conversion and lower CAC via trust signals and fewer step‑ups.
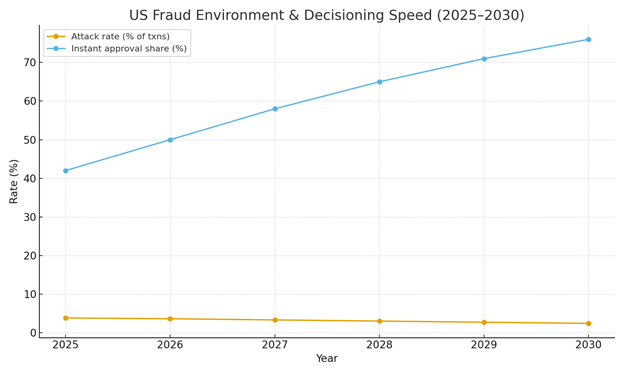
Market Analysis
Unit economics improve as false positives and manual reviews fall while approval latency shrinks. In this outlook, DTC retailers drive false positives from ~1.8% to ~0.9% and manual reviews from ~8% to ~3.5%; marketplaces see similar halving as seller KYC and payout controls mature; subscription apps converge on ~1.0% false positives and ~4% manual review. Median decision latency compresses to ~20–35 seconds, even with selective step‑up liveness. Cost drivers include data licensing (telco/device/payment tokens), model training/serving infra, and human review. Benefits: higher conversion, fewer chargebacks, lower labor, and stronger LTV from reduced insult rates.
Risk vectors evolve: ATO via SIM‑swap and OAuth abuse; synthetic IDs seeded with low‑risk spend; promo/returns fraud; and deepfake‑assisted document forgery. Mitigations: multi‑signal identity graphs; continuous behavioral profiling; cryptographic binding of sessions to devices; watermark/liveness for media uploads; and policy engines that throttle high‑risk promotions. Programs should be governed by clear SLAs (latency, FPR, review rate), quarterly red‑team tests, and bias audits with remediation plans.
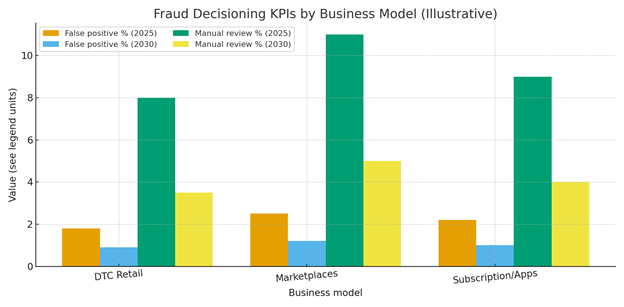
Trends & Insights (2025–2030)
• Behavioral biometrics at checkout and login measure micro‑movements, rhythm, and hesitation hard to spoof at scale.
• Deepfake detection pairs passive signals (blink, texture) with active prompts and server‑side liveness cryptograms.
• Identity graphs enrich with consented telco/device/payment tokens; graph features drive instant approvals.
• Privacy‑preserving techniques (federated learning, tokenization) reduce PII movement while improving accuracy.
• Real‑time policy engines coordinate price/promo abuse limits with fraud thresholds to cut arbitrage.
• Explainable decisions and adverse‑action workflows become procurement requirements.
• Shared threat intel across platforms (hashes, device clusters) shortens dwell time of new attacks.
• Managed fraud services grow for SMBs; enterprises retain control planes with vendor signals via APIs.
Segment Analysis
• DTC Retail: focus on promo/returns abuse and payment fraud; leverage device binding and address/identity validation; minimize friction with selective liveness for risky cohorts.
• Marketplaces: seller onboarding KYC, payout risk, and triangulation scams dominate; maintain continuous monitoring and velocity checks; verify bank/tax identities and monitor inventory flows.
• Subscription/Apps: account sharing and password spraying drive ATO; integrate telco signals and challenge flows for suspicious sessions; protect recurring billing against chargeback farms.
• BNPL/Alt‑pay: fast credit decisions heighten synthetic‑ID risk; require strong identity resolution and repayment telemetry.
Geography Analysis (United States)
Readiness is strongest in the Northeast and West where data talent, telco/payment partners, and platform vendors cluster; the South and Midwest gain as omnichannel commerce scales and carrier coverage improves. The stacked criteria—data signals, payment rails/alt‑pay, compliance readiness, carrier/device coverage, and organization/data talent—indicate where instant identity resolution can reach production SLAs first.
Implications: start rollouts in regions with robust signals and engineering capacity; co‑design consent and disclosures with legal; establish incident rollback paths; and maintain vendor diversity to avoid single‑point failures in signals or liveness.
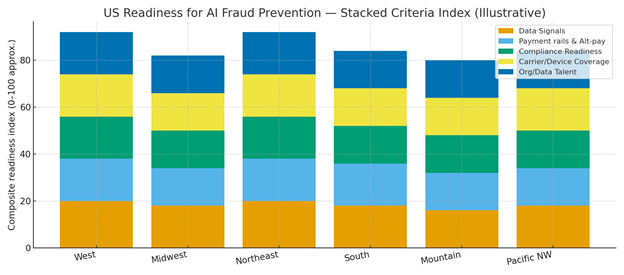
Competitive Landscape (Vendors & Operating Models)
The ecosystem includes behavioral biometrics providers, identity/liveness vendors, device and telco‑signal networks, graph risk platforms, and orchestration engines that route calls and manage policies. Differentiators: latency SLAs, breadth of consented signals, deepfake‑blocking efficacy, explainability, and integration to checkout/payout SDKs. Managed services bundle decisions for SMBs; enterprises construct control planes and swap signal vendors without code changes via adapters. Procurement shifts to outcome‑based contracts indexed to FPR, approval precision, latency, and verified deepfake catch‑rates. Winners publish audit trails, fairness metrics, and red‑team results, earning trust from risk and compliance while enabling marketing to move fast without compromising safety.
Report Details
Proceed To Buy
Want a More Customized Experience?
- Request a Customized Transcript: Submit your own questions or specify changes. We’ll conduct a new call with the industry expert, covering both the original and your additional questions. You’ll receive an updated report for a small fee over the standard price.
- Request a Direct Call with the Expert: If you prefer a live conversation, we can facilitate a call between you and the expert. After the call, you’ll get the full recording, a verbatim transcript, and continued platform access to query the content and more.


68 Circular Road, #02-01 049422, Singapore
Revenue Tower, Scbd, Jakarta 12190, Indonesia
4th Floor, Pinnacle Business Park, Andheri East, Mumbai, 400093
Cinnabar Hills, Embassy Golf Links Business Park, Bengaluru, Karnataka 560071
Request Custom Transcript
Related Transcripts


68 Circular Road, #02-01 049422, Singapore
Revenue Tower, Scbd, Jakarta 12190, Indonesia
4th Floor, Pinnacle Business Park, Andheri East, Mumbai, 400093
Cinnabar Hills, Embassy Golf Links Business Park, Bengaluru, Karnataka 560071













